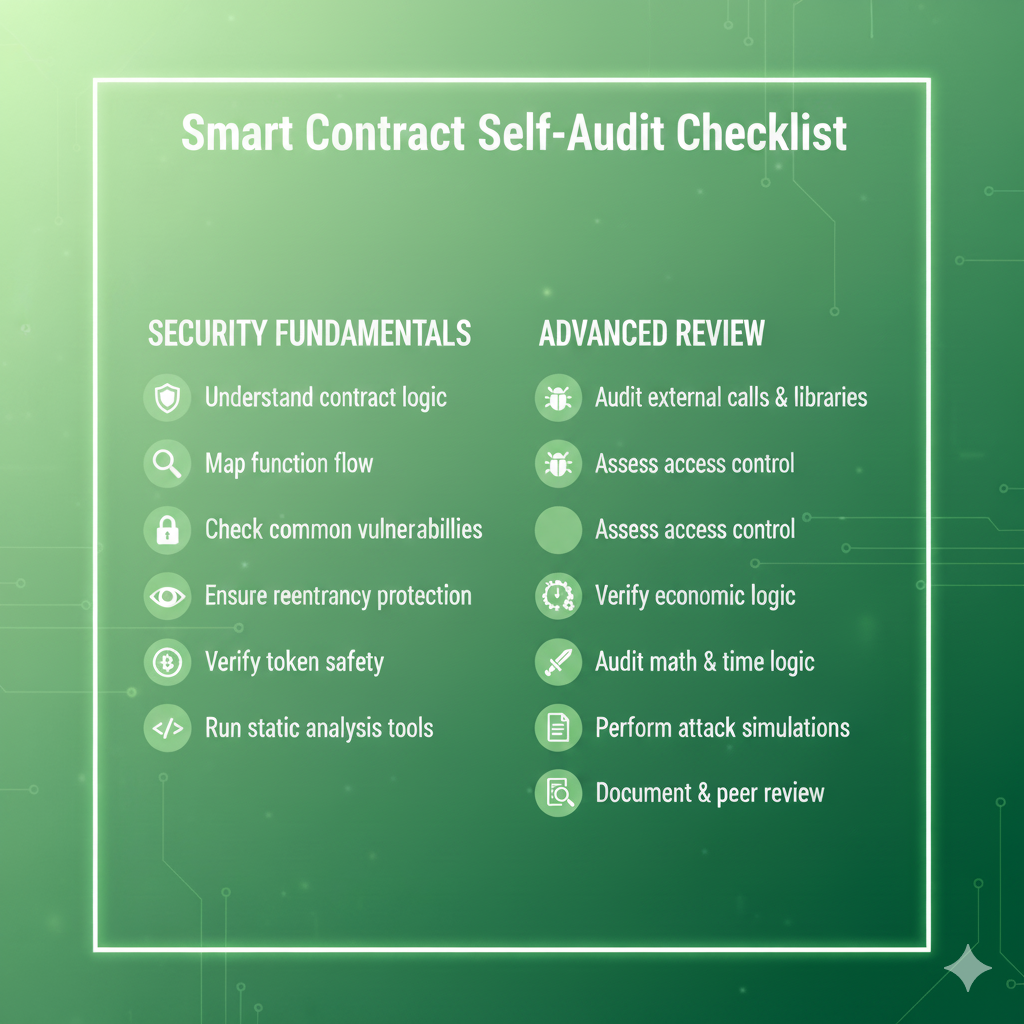
The Wild West of Web3 demands more than just innovation—it demands ironclad security. Every day, news feeds are ablaze with tales of millions vanishing in a flash—a testament to the catastrophic power of a single, tiny bug in a smart contract. If you’re building in this space, you’re sitting on a digital treasure chest, and every line of code is a potential lock or an open door for a sophisticated attacker.Forget outsourcing all your trust. Before you even think about deployment, you need to become your own first, best line of defense. We’ve cracked the code on the secrets the top Web3 security experts use—and we’re giving you the Smart Contract Self-Audit Checklist that can save your project from disaster! This isn’t just theory; this is a survival guide for the decentralized frontier.
Phase 1: The Deep Dive—Unmasking the Contract’s Secrets you can’t secure what you don’t truly understand. The first five steps are non-negotiable for anyone serious about security:
* Understand Contract Logic (The Architect’s View): This is where you lay the foundation. Can you, in simple terms, explain exactly what the contract is supposed to achieve? Before you check for bugs, ensure the contract’s overall intent aligns with your project’s goals. A security flaw can hide in a misunderstanding of what the code is meant to do.
* Map Function Flow (The GPS for Your Code): A contract isn’t a single entity; it’s a network of functions. Trace how data moves from one function to the next. What inputs does Function A take, and how does its output affect the state changes in Function B? This is critical for spotting unauthorized state changes or unexpected function execution paths.
* Check Common Vulnerabilities (The Hit List): You don’t need to reinvent the wheel. The industry has a list of notorious vulnerabilities. Actively hunt for them! This includes issues like integer overflow/underflow, denial-of-service vectors, and mishandled exception handling. Don’t be a victim of a well-known attack!
* Ensure Reentrancy Protection (The Death Blow Detector): Reentrancy attacks are the stuff of Web3 nightmares (hello, DAO hack!). This is where an external call can recursively call back into the original contract before the first execution is finished, draining its funds. Are you using the Checks-Effects-Interactions pattern? If you make an external call, you must ensure it can’t come back to haunt you.
* Verify Token Safety (The Asset Guard): If your contract handles tokens (ERC-20, ERC-721, etc.), are you correctly adhering to their standards? Check for approval issues, transfer logic, and potential unexpected behavior with tokens that have unique features like fee-on-transfer. Your asset handling must be flawless.
Phase 2: The Technical Arsenal—Tools and Tactics of the Pros once you’ve manually inspected the logic, it’s time to bring in the heavy hitters: automated tools and specialized checks.
* Run Static Analysis Tools (The Robot Auditor): Automated tools like Slither or Mythril are your best friends. They scan your code without executing it, identifying well-known security pitfalls, bad coding practices, and dangerous patterns. Treat their warnings as red flags requiring immediate investigation.
* Dudivect Tornos (Identify External Call Risks): While the original text contains a potential typo, the core intent here is vital: carefully audit all external calls and interfaces. Any time your contract interacts with another contract, you introduce an element of risk. Is the external contract trusted? What happens if that call reverts? What if it drains your gas limit? This is a prime attack vector.
* Essun Access Control / Reviw Access Control (The Gatekeeper’s Role): These two points (again, potentially slightly garbled in the source image but clear in intent) boil down to one thing: Who can do what? This is your access control audit. Is a function that only the contract owner should call protected by an only owner modifier? Can a regular user mint tokens? Every critical function must have a clearly defined and strictly enforced permission model. This is where most basic attacks begin!
* Audit Math & Time Logic (The Precision Check): Smart contracts are often used for financial calculations (stakes, distributions, fees). Are you handling division and multiplication correctly? Are you safe from common pitfalls with floating-point arithmetic (which Solidity doesn’t even support, forcing a more complex fixed-point approach)? Furthermore, never rely on block.timestamp for critical, time-sensitive functions, as miners can manipulate this within a small range!
Phase 3: The Ultimate Test—Proving Your ResilienceYou’ve checked the code, run the tools, and tightened the access controls. Now, it’s time for the final, brutal tests.
* Perform Attack Tests (The Trial by Fire): You need to think like a hacker. Execute fuzzing and unit tests specifically designed to break your code. Try to call functions out of order. Attempt to pass in extreme or zero values. Can you force an integer overflow? Can you bypass the require statements? If you can’t break it, a hacker probably can’t either.
* Document & Peer Review (The Sanity Check): Security isn’t a solo sport. Document your security decisions and have another pair of competent eyes—or better yet, an entire team—review your code. A peer review often catches subtle logical flaws that the original developer overlooked. This is your final quality gate before the spotlight hits.
Don’t Wait For Disaster—Act Now!Deploying an unaudited smart contract is like launching a rocket with a paper fuse. The risk is simply too high. This self-audit checklist isn’t just a list of steps; it’s a mindset. Adopt this rigorous but vital and necessary approach, and you’ll dramatically reduce your attack surface, safeguard your users’ funds, and cement your reputation as a builder of secure, reliable Web3 infrastructure. Ready to stop the hackers dead in their tracks? Start checking off this list today!